Rogue security software (aka FakeAV or Fake Antivirus) is a form of Internet fraud using malicious software (malware) that deceives or misleads users into paying money for fake or simulated removal of malware. Typically these programs do not have a virus definition database nor a virus scan engine. All of the processes of a security program are imitated to scare victims into believing that their computers are infected with critical risk malware and viruses.
Since 2008 FakeAV is one of the most common malware families that HitmanPro finds on computers protected by an up-to-date antivirus program. The reason for this is that security vendors have a hard time keeping up with the cybercriminals who obfuscate and release new versions and variants of their annoying creations almost every day. Each iteration also has a deceiving name like Security Shield and Live Security Platinum. And to further lure victims into paying money, most rogue security software protect themselves by preventing legitimate programs from starting – this includes productivity software, internet security software and rescue tools. So you can imagine why FakeAV still takes the #1 position on our Malware Prevalence Top 25 month after month.
Rootkit
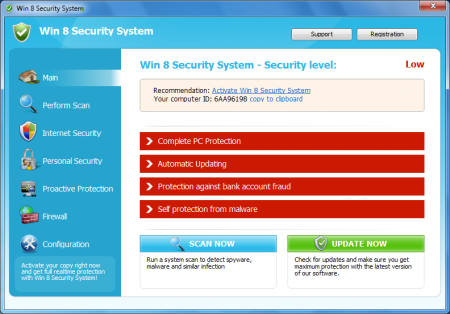
The reason for writing this article is that we found a new FakeAV which takes a different approach of deceiving and frustrating its victims. This new FakeAV is called Win 8 Security System:
Unlike its predecessors this FakeAV comes with a special rootkit driver which monitors and manipulates the operating system, taking control of every other process and program on the computer. One of the main purposes of the rootkit is to repair the FakeAV program (make it stick to the machine) and to make removal complicated.
The recognition of the rootkit driver is currently very low, only 1 out of 42 renowned anti-virus programs are capable of identifying this rootkit:
The rootkit driver is installed in the Windows drivers folder and has a random name, e.g. C:\Windows\system32\drivers\51991c15f7a6834.sys
64-bit Driver
The malware installs a different driver on computers running 64-bit Windows and disables 64-bit kernel-mode driver signing on these machines. Nonetheless, the cybercriminals went an extra mile by self-signing it with a certificate. Note the validity period, which starts on August 30 (yesterday):
Fake Action Center
The malware shows a fake Action Center, telling the victim the computer is not properly protected against viruses and spyware. When you want to open the real Action Center from the Control Panel, the malware will open the fake one instead:
Browser Hijacker
FakeAV often configures the proxy settings of your computer to intercept web browsing. This malware is different and uses its rootkit to hijack Internet Explorer and Google Chrome to display fake security warning messages when you try to browse the Internet:
Shortcuts
Interestingly, shortcuts that belong to the malware (created on the Start Menu and on the Desktop) all link to the Windows command-line registry editior reg.exe. When the victim clicks on, for example, the Buy Win 8 Security System shortcut, a harmless registry entry is created, which is monitored by the rootkit.
- Target: C:\WINDOWS\system32\reg.exe add “HKCU\SOFTWARE\Microsoft\Windows NT” /v FrameworkBuild /t REG_DWORD /d 0 /f
When this registry value is accessed (when you click on the shortcut), the rootkit is triggered and opens the shopping cart:
As you can see, for security software this FakeAV is pretty expensive. And if you pay, you have not only paid 100 bucks for fake software, you also submitted your credit card details to the cybercriminals.
Domains
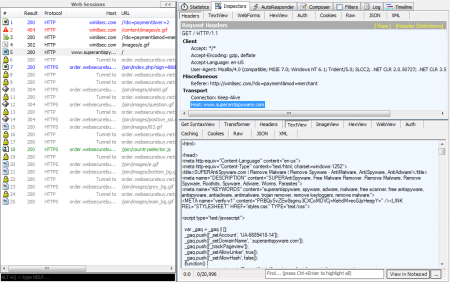
When you look at the web traffic when the shopping cart opens, you can see some other interesting things:
The first site that is accessed is win8sec.com; the malware added this domain as a trusted domain to your computer upon installation. Next it communicates with the http://www.superantispyware.com domain, which belongs to a known legitimate anti-spyware program. If you compare the two websites you can see that win8sec.com is a partial copy of superantispyware.com:
When you lookup the win8sec.com domain record you can discover that it was registered not too long ago, on August 18, 2012 (the registrant details are fake):
The win8sec.com domain currently points to IP address 31.184.244.59. This address currently resides in the United Arab Emirates.
Solution
At time of this blog post, there is currently no anti-virus, anti-spyware or anti-malware tool that we know of that is capable of removing this malware completely. So some security forums are offering a comprehensive step-by-step tutorial, involving the use of multiple tools, to handle this infection. But many forget the rootkit component.
In the meantime, you can use HitmanPro (and the free license that comes with it) to thoroughly and conveniently remove the FakeAV program and its rootkit component. A screenshot of HitmanPro detecting this malware on a 64-bit computer:
Also, if you are affected by this malware, it is very likely that another malicious program was responsible for installing this FakeAV on your machine and is currently still hiding. You can also use HitmanPro to reveal and remove this hidden malware.









You must be logged in to post a comment.